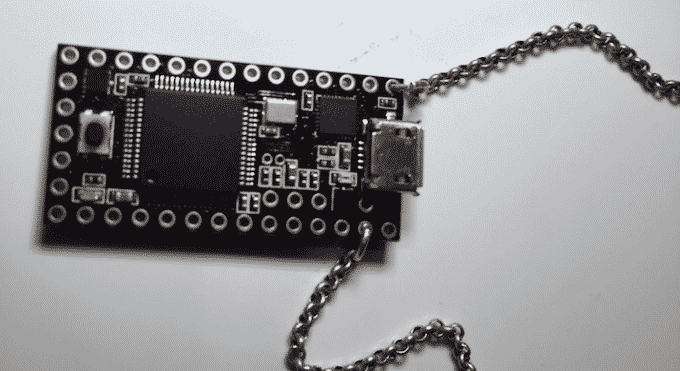
It is that scene in every movie where the spy breaks into the “computer room” and inserts a USB key that instantly brings down the system or security. While you may think a device like this could never be real, the scary thing it is!
Friend of ThinkComputers, Samy Kamkar has created this unique device. If you haven’t heard of Samy he is behind such exploits as the massive MySpace worm in 2006 and SkyJack – a drone that can hack and control other drones. He has created a USB device that he sometimes wears around on a necklace. In the video below he goes over just how the USB necklace can hack your system.
Samy calls the device USBDriveBy and it is a USB microcontroller that once plugged in to a USB port on your computer it can do the following things automatically:
– It starts by pretending to be a keyboard/mouse.
– If you have a network monitor app like Little Snitch running, it uses a series of keystrokes to tell LittleSnitch that everything is okay and to silence all warnings.
– It disables OS X’s built-in firewall.
– It pops into your DNS settings and tweaks them to something under the hacker’s control, allowing them to replace pretty much any website you try to visit with one of their own creation.
– It opens up a backdoor, then establishes an outbound connection to a remote server which can send remote commands. Since the connection is outbound, it eliminates the need to tinker with the user’s router port forwarding settings.
– It closes any windows and settings screens it opened up, sweeping up its footprints as it heads for the door.
So in just about 60 seconds it takes control on your machine, disables the security, cleans up it tracks and opens a connection for control of the machine even after the device has been removed, quite slick!
While Samy mainly focuses on OS X in his videos the same principles can be used to make the device work for Windows or Linux. So how can you prevent your system from becoming vulnerable to a device like this? The way the USB protocol is designed makes it very hard to protect your system from such an attack. We would suggest just keeping an eye on your USB ports!
Source: TechCrunch | News Archive